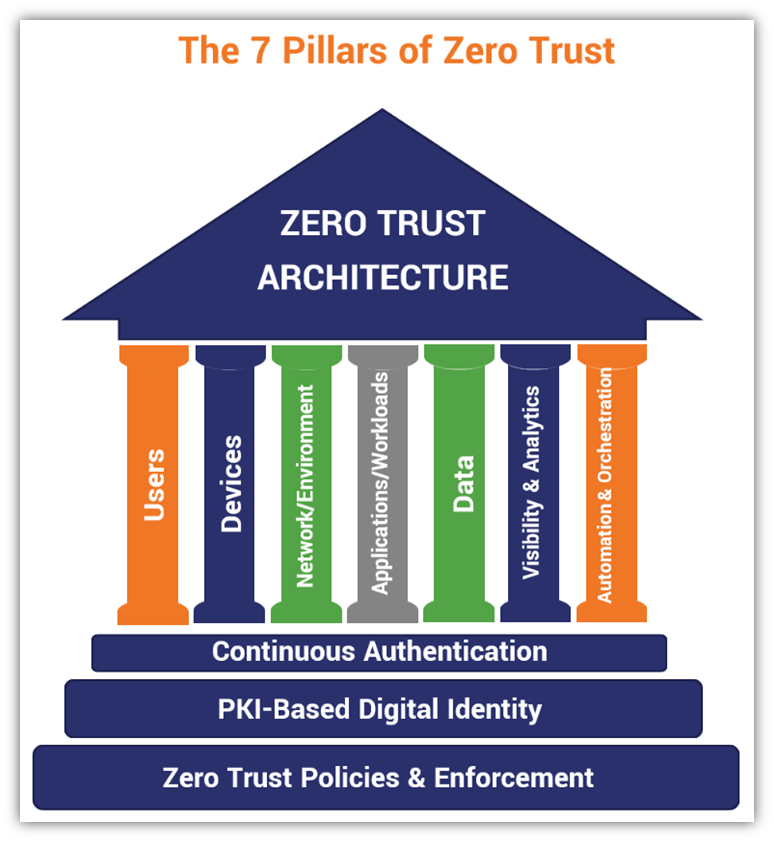
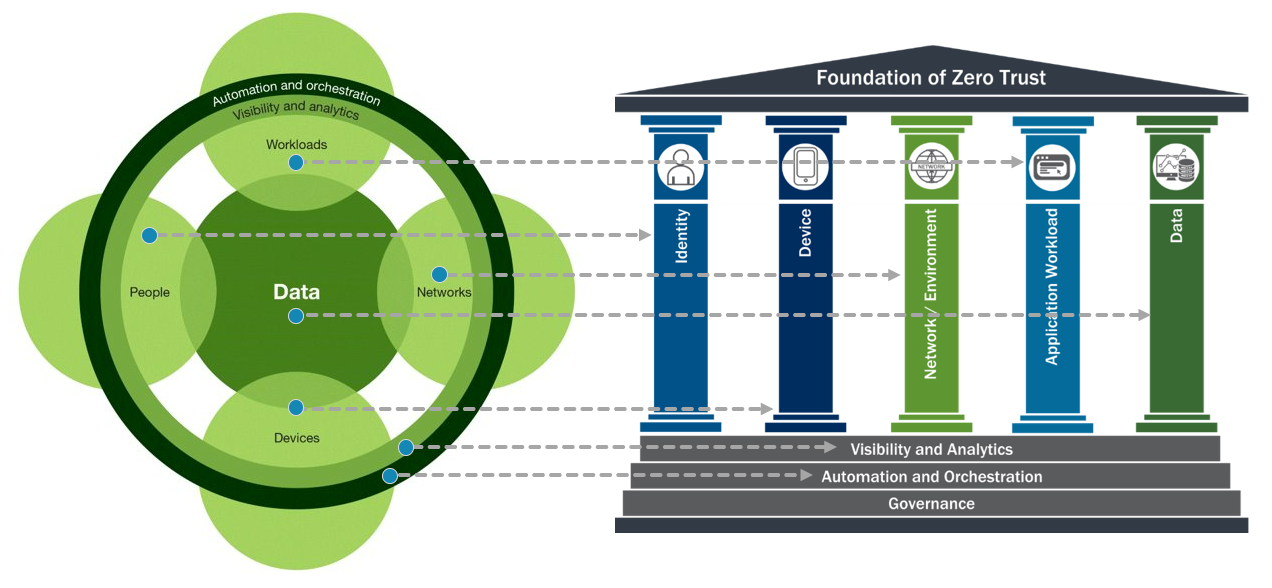
Antwort What are the 7 pillars of zero trust architecture? Weitere Antworten – What are the seven pillars of zero trust
The seven pillars are: User, Device, Network & Environment, Application & Workload, Data, Automation & Orchestration, and Visibility & Analytics. Each pillar requires certain criteria and objectives to achieve ZT enactment.The five pillars of the Zero Trust Maturity Model are: Identity; Devices; Network, Data, and Applications and Workloads.The six pillars of Zero Trust: Never trust, always verify!
- Trusted identities. Protect user access and keep control of device identities to secure the digital journey.
- Endpoint protection.
- Network security.
What are the core components of zero trust : Key components of a zero trust architecture
- Identity and access management.
- Secure access service edge.
- Data loss prevention.
- Security information and event management.
- Enterprise resource ownership catalog.
- Unified endpoint management.
- Policy-based enforcement points.
- Section summary.
What is Zero Trust framework
Zero Trust is a security framework requiring all users, whether in or outside the organization's network, to be authenticated, authorized, and continuously validated for security configuration and posture before being granted or keeping access to applications and data.
What are the 3 foundational concepts of zero trust : 3 Foundational Elements of Zero Trust You Can't Do Without
- Least Privilege. The concept of “never trust, always verify” is rooted in only allowing the right person to access the approved resources.
- Change Monitoring/Management.
- Configuration Monitoring/Management.
- Ensuring the “Zero” in Zero Trust.
Zero trust provides a collection of concepts and ideas designed to minimize uncertainty in enforcing accurate, least privilege per-request access decisions in information systems and services in the face of a network viewed as compromised.
3 Foundational Elements of Zero Trust You Can't Do Without
- Least Privilege. The concept of “never trust, always verify” is rooted in only allowing the right person to access the approved resources.
- Change Monitoring/Management.
- Configuration Monitoring/Management.
- Ensuring the “Zero” in Zero Trust.
What are the three main elements of a Zero Trust implementation
3 Foundational Elements of Zero Trust You Can't Do Without
- Least Privilege. The concept of “never trust, always verify” is rooted in only allowing the right person to access the approved resources.
- Change Monitoring/Management.
- Configuration Monitoring/Management.
- Ensuring the “Zero” in Zero Trust.
The main concept behind the zero trust security model is "never trust, always verify", which means that users and devices should not be trusted by default, even if they are connected to a permissioned network such as a corporate LAN and even if they were previously verified.7 Steps to Building Your Zero Trust Security Strategy
- Use Identities to Control Access.
- Adopt a User-Centric Approach.
- Incorporate Passwordless Authentication.
- Segment Your Corporate Network.
- Segment Your Applications.
- Secure Your Devices.
- Define Roles and Access Controls.
5 Steps to Building a Zero Trust Strategy
- Step #1. Verify trust upon access to any network resource – and do it in real-time.
- Step #2. Define trust, especially when it comes to devices.
- Step #3. Personalize your security posture with a user-centric approach.
- Step #4. Collect use cases.
- Step #5. Gradually expand.
Which three 3 of these are core principles of Zero Trust : As business and technology continue to evolve, the three core principles of Zero Trust security remain consistent. Never trust. Always verify. Implement Zero Trust security for your business.
What are the three main elements of a zero trust implementation : 3 Foundational Elements of Zero Trust You Can't Do Without
- Least Privilege. The concept of “never trust, always verify” is rooted in only allowing the right person to access the approved resources.
- Change Monitoring/Management.
- Configuration Monitoring/Management.
- Ensuring the “Zero” in Zero Trust.
Which three 3 of practices are core principles of zero trust
As business and technology continue to evolve, the three core principles of Zero Trust security remain consistent. Never trust. Always verify. Implement Zero Trust security for your business.