Antwort What are the six pillars of zero trust? Weitere Antworten – What are the 6 pillars of zero trust
The six pillars of Zero Trust: Never trust, always verify!
- Trusted identities. Protect user access and keep control of device identities to secure the digital journey.
- Endpoint protection.
- Network security.
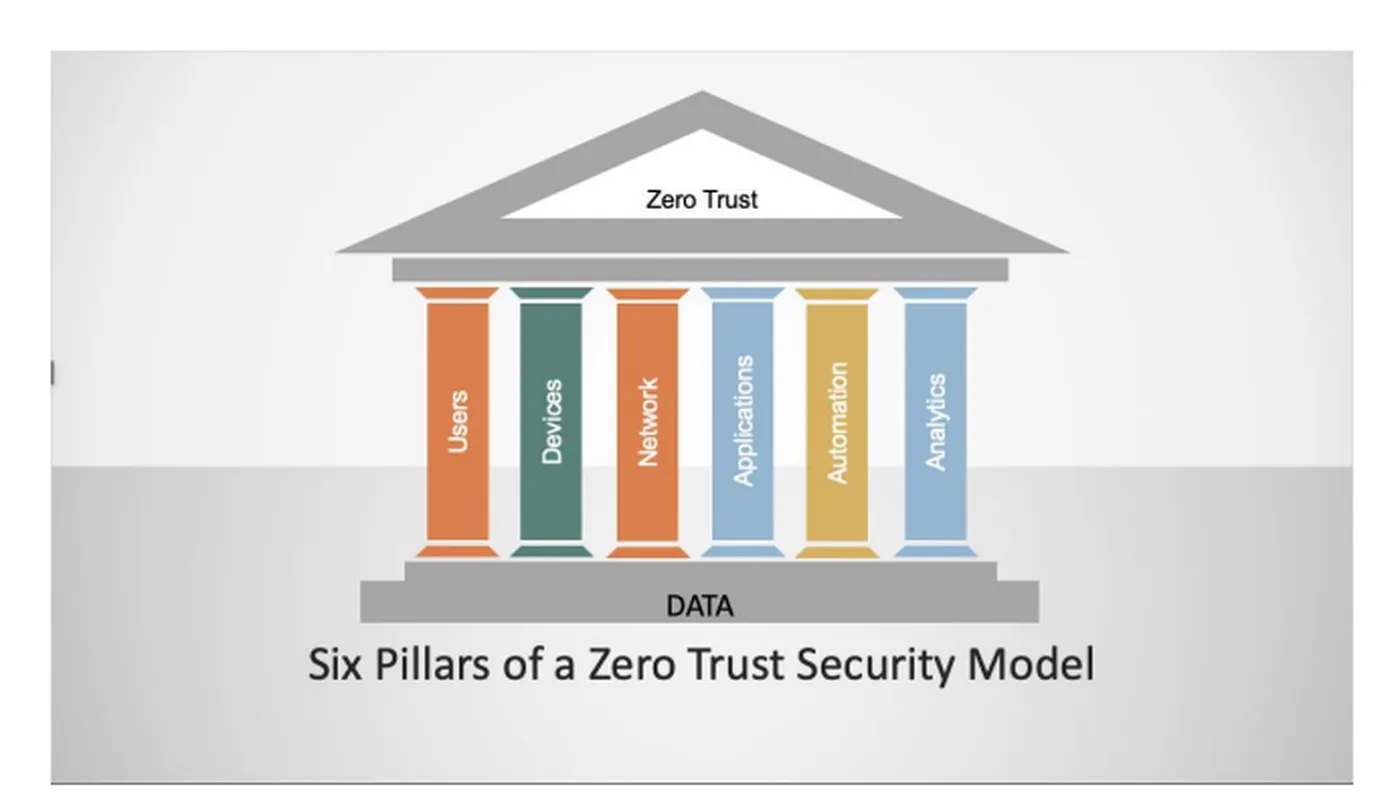
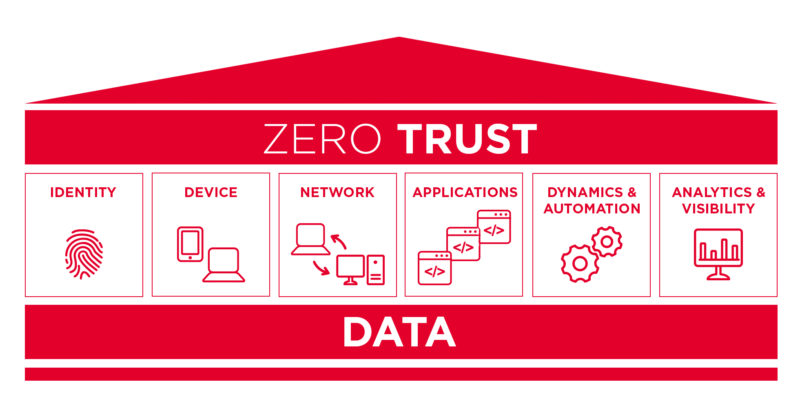
The seven pillars are: User, Device, Network & Environment, Application & Workload, Data, Automation & Orchestration, and Visibility & Analytics. Each pillar requires certain criteria and objectives to achieve ZT enactment.Key components of a zero trust architecture
- Identity and access management.
- Secure access service edge.
- Data loss prevention.
- Security information and event management.
- Enterprise resource ownership catalog.
- Unified endpoint management.
- Policy-based enforcement points.
- Section summary.
What are the 5 tenets of DOD zero trust : These include: 1) Assume a Hostile Environment; 2) Presume Breach; 3) Never Trust, Aways Verify; 4) Scrutinize Explicitly; and 5) Apply Unified Analytics. Reduce Complexity. Align technical and security programs with ZT goals and mission objectives to streamline regulations and standards for managing security and risk.
What is the six pillars approach
The paper describes six foundational concepts (the used future, the disowned future, alternative futures, alignment, models of social change, and uses of the future), six questions (will, fear, missing, alternatives, wish, and next steps as related to the future) and six pillars (mapping, anticipating, timing, …
What is Zero Trust framework : Zero trust provides a collection of concepts and ideas designed to minimize uncertainty in enforcing accurate, least privilege per-request access decisions in information systems and services in the face of a network viewed as compromised.
There are three key components in a zero trust network: user/application authentication, device authentication, and trust.
3 Foundational Elements of Zero Trust You Can't Do Without
- Least Privilege. The concept of “never trust, always verify” is rooted in only allowing the right person to access the approved resources.
- Change Monitoring/Management.
- Configuration Monitoring/Management.
- Ensuring the “Zero” in Zero Trust.
What is zero trust framework
Zero Trust is a security framework requiring all users, whether in or outside the organization's network, to be authenticated, authorized, and continuously validated for security configuration and posture before being granted or keeping access to applications and data.The five pillars of the Zero Trust Maturity Model are: Identity; Devices; Network, Data, and Applications and Workloads.The Six Pillars of Character® are core values that people follow to conduct themselves ethically in any organization. These ethical values transcend such belief structures as religion and politics to help guide ethical decision-making in business.
These are: trustworthiness, respect, responsibility, fairness, caring, and citizenship. A further definition of each is below. Trustworthiness: be honest, be reliable, have the courage to do the right thing, build a good reputation, and be loyal.
What is Zero Trust roadmap : A Zero Trust framework requires that users only have access to specific segments of the network required to complete a given task. Zero Trust Network solutions allow users to access a local network remotely but, with granular policies based on user, device and other factors.
What is the basic of Zero Trust : Zero Trust security means that no one is trusted by default from inside or outside the network, and verification is required from everyone trying to gain access to resources on the network. This added layer of security has been shown to prevent data breaches.
How do you build a successful Zero Trust strategy
7 Steps to Building Your Zero Trust Security Strategy
- Use Identities to Control Access.
- Adopt a User-Centric Approach.
- Incorporate Passwordless Authentication.
- Segment Your Corporate Network.
- Segment Your Applications.
- Secure Your Devices.
- Define Roles and Access Controls.
3 Foundational Elements of Zero Trust You Can't Do Without
- Least Privilege. The concept of “never trust, always verify” is rooted in only allowing the right person to access the approved resources.
- Change Monitoring/Management.
- Configuration Monitoring/Management.
- Ensuring the “Zero” in Zero Trust.
We will talk about trustworthiness respect responsibility fairness caring and citizenship. These are often referred to as the six pillars of character.
What is zero trust strategies : Zero Trust is a strategic approach to cybersecurity that secures an organization by eliminating implicit trust and continuously validating every stage of a digital interaction.